CBOM vs SBOM: Understanding the Key Differences in Software Security

Today, software security problems go beyond just having insecure code or missing patches. Today’s risks often come from what software is made of and how important security features like cryptography are used. Because of this, more companies are using bills of materials to improve visibility into their software environments.
Most security teams now know about SBOMs, which are documents that list the parts and dependencies of software. But a newer concept called CBOM is gaining attention as businesses realise that cryptographic weaknesses can be just as damaging as vulnerable libraries. There’s a growing discussion around CBOM vs SBOM and how these two approaches are different in terms of purpose and value.
This blog explains the main differences between CBOM and SBOM, where each fits into software security programs, and why mature organisations are beginning to treat them as complementary instead of interchangeable.
What SBOM Focuses on in Software Security
A software bill of materials (SBOM) lists all the software components that an application uses. It documents open-source libraries, third-party dependencies and internal packages, making it clear how software is assembled.
From a security perspective, SBOMs are used to:
-
Identify vulnerable components quickly
-
Keep track of where and when dependencies come from
-
Help speed up the analysis of vulnerability impacts
-
Make the software supply chain visibility
SBOMs list what software components exist and where risk may be inherited from external sources.
What CBOM Focuses on in Software Security
CBOM looks at a different but equally important part of risk.
A CBOM (Cryptographic Bill of Materials) is a list of cryptographic assets and implementations used in software systems. Instead of libraries or packages, it focuses on how cryptography is actually used.
A CBOM usually records:
-
Cryptographic algorithms in use
-
Key lengths and configurations
-
Certificates and their lifecycles
-
Cryptographic libraries and implementations
-
Key management and storage mechanisms
In the CBOM vs SBOM comparison, CBOM tells you how security controls are implemented, not just which components are present.
The Core Difference Between CBOM And SBOM
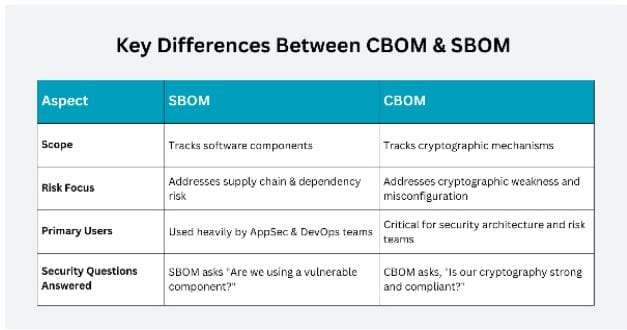
At a high level, the difference between CBOM and SBOM comes down to composition versus protection.
Key differences include:
-
Scope: SBOM keeps track of software components, while CBOM tracks cryptographic mechanisms.
-
Risk Focus: SBOM addresses supply chain and dependency risk, while CBOM addresses cryptographic weakness and misconfiguration.
-
Primary Users: SBOM is used heavily by AppSec and DevOps teams, while CBOM is critical for security architecture and risk teams
-
Security Questions Answered: SBOM asks “Are we using a vulnerable component?” while CBOM asks, “Is our cryptography strong and compliant?”
Both deal with different levels of software security.
Why SBOM Cannot Replace CBOM
A lot of companies think that SBOMs are enough to see what’s going on with software security. In reality, this assumption creates blind spots.
SBOMs don’t reveal:
-
Encryption algorithms that are weak or deprecated
-
Expired or mismanaged certificates
-
Cryptographic settings that aren’t secure
-
Hardcoded keys or poor key rotation practices
This is an important point in the CBOM vs SBOM debate: SBOMs show what code exists, but they don’t explain how cryptography behaves at runtime.
Why CBOM Cannot Replace SBOM
The reverse is also true – CBOMs alone are not enough.
CBOMs do not provide insight into:
-
Weak open-source dependencies
-
Supply chain compromise risks
-
Licensing and provenance issues
-
Transitive dependency exposure
It’s not a choice between two competing tools. Each one addresses a different type of risk, and neither can fully replace the other.
How Attackers Exploit Gaps Between CBOM And SBOM Visibility
Attackers rarely depend on a single weakness. They often take advantage of multiple gaps across different layers.
In real life, attackers might:
-
Use a weak dependency to gain initial access (SBOM gap)
-
Abuse weak cryptographic configurations to escalate or persist (CBOM gap)
-
Exploit expired certificates or poor key hygiene to evade detection.
Without visibility across both domains, organisations find it hard to see full attack paths. This is why the CBOM vs SBOM comparison is best viewed through a combined-risk lens.
Operational Challenges in Managing CBOM vs SBOM
Managing either bill of materials introduces complexity. Managing both requires coordination.
Some common challenges are:
-
Generating accurate data on a large scale
-
Updating inventories as systems change
-
Assigning ownership across teams
-
Integrating findings into security processes
-
Avoiding duplication or conflicting data
Companies that treat CBOM and SBOM as isolated initiatives often fail to realise their combined value.
How Mature Companies Use CBOM And SBOM Together
Mature security programs integrate both approaches into a unified visibility strategy.
In practice, this means:
-
Using SBOMs to find vulnerable parts early
-
Using CBOMs to check compliance and cryptographic strength
-
Correlating findings to understand real exploitability
-
Prioritising remediation based on combined risk
This integrated approach turns the CBOM vs SBOM discussion from comparison into collaboration.
Compliance And Regulatory Implications of CBOM vs SBOM
Regulators increasingly expect evidence of software transparency and cryptographic robustness.
SBOMs support:
-
Software supply chain transparency
-
Third-party risk assessments
-
Vulnerability disclosure response
CBOMs support:
-
Cryptographic compliance requirements
-
Algorithm strength validation
-
Certificate and key lifecycle governance
Together, they strengthen audit readiness and reduce compliance friction.
When Organisations Should Prioritise CBOM, SBOM or Both
While both are important, priorities may differ based on risk profile.
Organisations should prioritise:
-
SBOMs when managing open-source-heavy applications
-
CBOMs when handling sensitive or regulated data
-
Both when operating complex, business-critical software environments
In most modern enterprises, the answer to CBOM vs SBOM is increasingly “both.”
Next Steps
Organisations evaluating their software security posture should assess whether current visibility covers both dependency risk and cryptographic risk. In many cases, teams have adopted SBOMs but lack insight into how cryptography is implemented across systems.
A structured approach to CBOM & SBOM integration helps organisations close this gap. CyberNX is a cybersecurity firm help organisations integrate SBOM and CBOM into practical security programs that deliver real visibility. If cryptography feels like a blind spot in your environment, you must address it sooner rather than later.
Conclusion
The debate around CBOM vs SBOM is not about choosing one over the other. SBOMs provide visibility into software components and supply chain risk, while CBOMs expose cryptographic weaknesses that can undermine security even in well-maintained systems.
As software ecosystems grow more complex and attackers exploit layered weaknesses, organisations need both perspectives to defend effectively. Understanding the key differences between CBOM and SBOM – and using them together – has become very important for modern software security.
Media Contact
Company Name: Cybernx
Email: Send Email
City: New York
Country: United States
Website: https://www.cybernx.com/


